Server Configuration
Each server to which the SRP must synchronize its working directory is configured in the SRP GUI through the Admin page. To configure the existence of a SRP node, add the necessary information to the Administration screen:
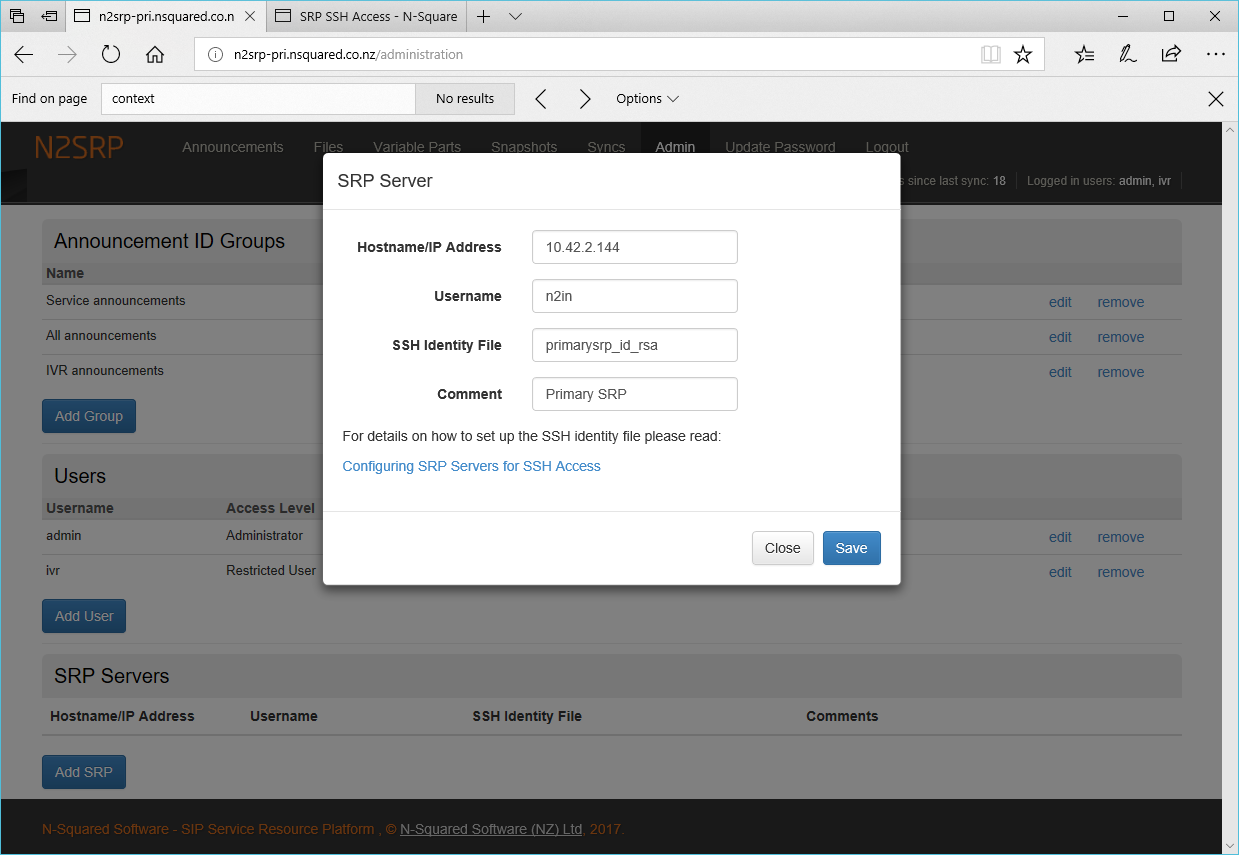
When configuring the SRP server, the following fields need to be configured:
| Field | Description |
|---|---|
| Hostname/IP Address | The hostname or IP address of the server. |
| Username | The user to connect to the server with using SSH. This should usually be `n2in`. |
| SSH Identify File |
If a unique SSH private key file is to be used for this connection, the full path to this file is required.
If this file is not provided, the web-server user on the primary SRP is expected to be able to ssh to the host defined as the user given and log in without a password. This would usually require the private key to be the web-server user’s default one (i.e. `~/.ssh/id_rsa`). |
| Comment | An optional comment describing the server. |
Prior to configuring a SRP Server in the above GUI however, the passwordless SSH login to the SRP server must be configured. This is achieved through the use of a private/public SSH key pair, accessible to the UNIX user who executes the SRP management interface user interface (under Linux this will be www-data or httpd, depending on the target platform).
To configure the login for a SRP server, follow these steps:
- Log in to the primary SRP.
- As a root user, or a user with
sudoaccess, set up the directory where the private key is to be stored, e.g:
sudo mkdir -p /var/lib/n2srp/etc
cd /var/lib/n2srp/etc
chmod 700 /var/lib/n2srp/etc
- Run the following command to create the public and private key:
sudo ssh-keygen -t rsa
The following example interaction shows the creation. Note that when asking for a passphrase, press enter to give an empty passphrase:
# ssh-keygen -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (//.ssh/id_rsa): /var/lib/n2srp/etc/srp_id_rsa
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /var/lib/n2srp/etc/srp_id_rsa.
Your public key has been saved in /var/lib/n2srp/etc/srp_id_rsa.pub.
The key fingerprint is:
c7:39:82:41:ba:2d:3a:53:f8:38:48:e7:7d:64:02:2e root@n2srp-pri
- Update ownership of the file, ensuring it is available to the web server account only:
chown -R www-data:www-data /var/lib/n2srp/etc
- Copy the public key file to the remote server, to the n2in account:
scp /var/lib/n2srp/etc/srp_id_rsa.pub n2in@srp-server:
- Log in to the SRP server, and configure the
~/.ssh/authorized_keysfile:
ssh n2in@srp-server
mkdir .-p ssh
chmod 700 .ssh
- Add the new key to the
authorized_keysfile. Note that you may need to edit the authorized key string to adjust the host and/or user the authorized key is for.
cat srp_id_rsa.pub >> .ssh/authorized_keys
chmod 600 .ssh/authorized_keys
chown -R n2in:daemon .ssh
rm srp_id_rsa.pub
- Return to the server hosting the SRP GUI, and test login to the remote server:
su www-data -s `which bash`
ssh -i /var/lib/n2srp/etc/srp_id_rsa n2in@srp-server
This may display the following warning:
The authenticity of host 'primarysrp (10.42.2.152)' can't be established.
RSA key fingerprint is 43:e0:5b:fd:5a:cb:02:14:b4:28:ca:6b:2f:90:d0:ee.
Are you sure you want to continue connecting (yes/no)?
If this is displayed, type yes<enter> to continue. There should be no request for any other interaction. In particular, there should be no password request.
- If the following error occurs:
Failed to add the host to the list of known hosts (/var/www/.ssh/known_hosts).
Create the directory /var/www/.ssh/ so that the known_hosts file can be created, and ensure that this directory is owned by the user www-data.
In addition, various restrictions may limit the ability for the client to log in. Always:
- Ensure that the
n2inuser is in the ssh daemon configuration forAllowUsers. - Ensure the
sshdaemon configuration ofPermitEmptyPasswordsis set to yes. - Ensure that the user
n2incan log in to the server. This can be updated usingusermod -s `which bash` n2inas root, on the target server.
You can now configure the SRP server in the administration page. When configuring the SRP server ensure the username is set to the correct username to log in to the remote server, and that the SSH Identify File field is set to the path of the private key file created.